During the last years IDS/IPS technology has helped to detect malicious activity not only in the server side but also in the clients side. Actually, we experience an increasing volume of attacks on the clients side, criminals finds easier to target users and one of the most used attack vectors is the email with a link to an exploitkit or attached file.
With IPS/IDS technologies we have been able to identify ifected users machines, basically because in most cases the protocol used was HTTP. Nowadays things are changing and attackers and improving their infrastructure implementing SSL channels, which makes harder to detect them. The response from the industry have been, basically this 2 aproaches:
SSL inspection (Man-in-the-Middle)
If the company has a corporate proxy, it is possible to intercept the SSL. There are comercial solutions, but it is possible to implement it with open source software like Squid using SslBump Peek and Splice configuration. The only requirement is the client, trusts the CA that generates the certificates in the proxy.
When the user wants to connect using HTTPS, the proxy will establish a connection to the real server and will negociate another channel with the client. Once we have the plain traffic, we can use ICAP or we can mirror the decrypted traffic to the IDS.
The amount of resources required for this aproach will depend on the number of users using the proxy. As most of the traffic on the Internet is HTTPS, the hardware requirements for the cryptographic functions (decrypt and encrypt for each connection) will be quite expensive.
JA3 and JA3S (Connection fingerprint)
The JA3/JA3S algorithm takes a collection of settings from the SSL “Client Hello” such as SSL/TLS version, accepted cipher suites, list of extensions, accepted elliptic curves, and elliptic curve formats. For compactness the string is hashed with MD5. JA3 is intended to identify the client and JA3S the server.
Trickbot malware
- JA3 = 6734f37431670b3ab4292b8f60f29984 ( Trickbot )
- JA3S = 623de93db17d313345d7ea481e7443cf( C2 Server Response )
Emotet malware
- JA3 = 4d7a28d6f2263ed61de88ca66eb011e3 ( Emotet )
- JA3S = 80b3a14bccc8598a1f3bbe83e71f735f ( C2 Server Response )
JA3 was created at Salesforce by:
- John Althouse
- Jeff Atkinson
- Josh Atkins
With this approach, we will not be able to analyze the crypted traffic but we will identify the connection is related to a malicious activity.
Neverwave: browser extension
Neverwave uses completely different approach. It is a browser plugin compatible with Google Chrome, Chromium, Microsoft Edge, Opera Browser, Brave and other Chromium based browsers. It will detects attacks in the early stage of the infection process.
As it is a plugin, it doesn’t need to decrypt the traffict, it can process the data before it’s encrypted.
At the moment it blocks:
- Exploitkits like GrandSoft, KaiXin , Magnigate/Magnitude, Purple Fox, RIG, Router … among others.
- Compromised sites that may be harmful.
- Generic exploit patterns related to known vulnerabilities like CVE-2018-8174 or CVE-2018-8373 among others.
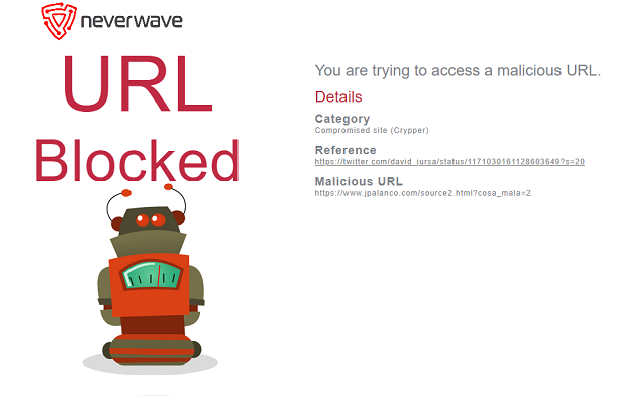
For implementing this I used patterns for Emerging Threats, Snort and EKFiddle
You can install it for free in your chromium compatible browser from the Chrome Web Store:
 Jose Ramon Palanco
Jose Ramon Palanco 

 Pentesting iOS Apps with OSX and a Jailbroken device
Pentesting iOS Apps with OSX and a Jailbroken device